Implementing SAML to XACML

Before Implementing SAML
This is how a XACML request will looks like when it is arriving at PDP(Policy Decision Point) to be evaluated.Basically it states who is(Subject) wanting to access which resource and what action it wants to perform on the resource. PDP trusts that request made is not altered while being sent and received, evaluates the request against existing enabled policies and reply with the decision which will be as follows.
Again there is no guarantee for the party who is using this response that this decision is not altered since sent from PDP until been received.
In order achieve the security of XACML requests and responses in server to server communication SAML profile for XACML is defined by OASIS.This take the system security to a higher level by allowing the usage of fine-grained authorization provided by XACML, to be signed.
After Implementing SAML

Following is how the previous XACML request looks like after wrapped into a XACMLAuthzDecisionQueryType, which is generated using OpenSAML 2.0.0 library which is supporting SAML profile of XACML as declared in 2004. The diagram shows the basic structure of a XACMLAuthzDecisionQueryType.

Following is a sample XACMLAuthzDecisionQuery.
As you can see it carries lot of information related to the content of the request like who issued it , when, signature with the X509Certificate and the XACML request. Data integrity can be preserved in this way.
After executing the request and gaining the response from PDP, it is also sent secured with a signature. The diagram shows the structure of a basic SAML Response.
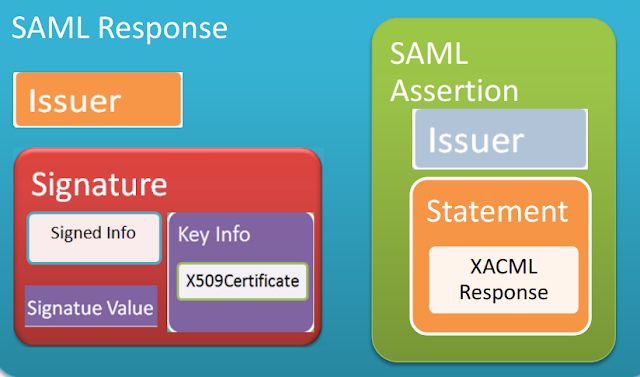
Following is a sample SAML response that carries XACML response.
The XACML response is wrapped into a SAML statement which is included in a SAML assertion that is again wrapped by a SAML response.I have only signed the response according to the context and included only one assertion. We can separately sign both the assertion and response according to the spec and include more assertions in one response. Also it is possible to send the relevant XACML request inside the response and lot more options are there according to the spec. With OpenSAML we can get most of them into action.


